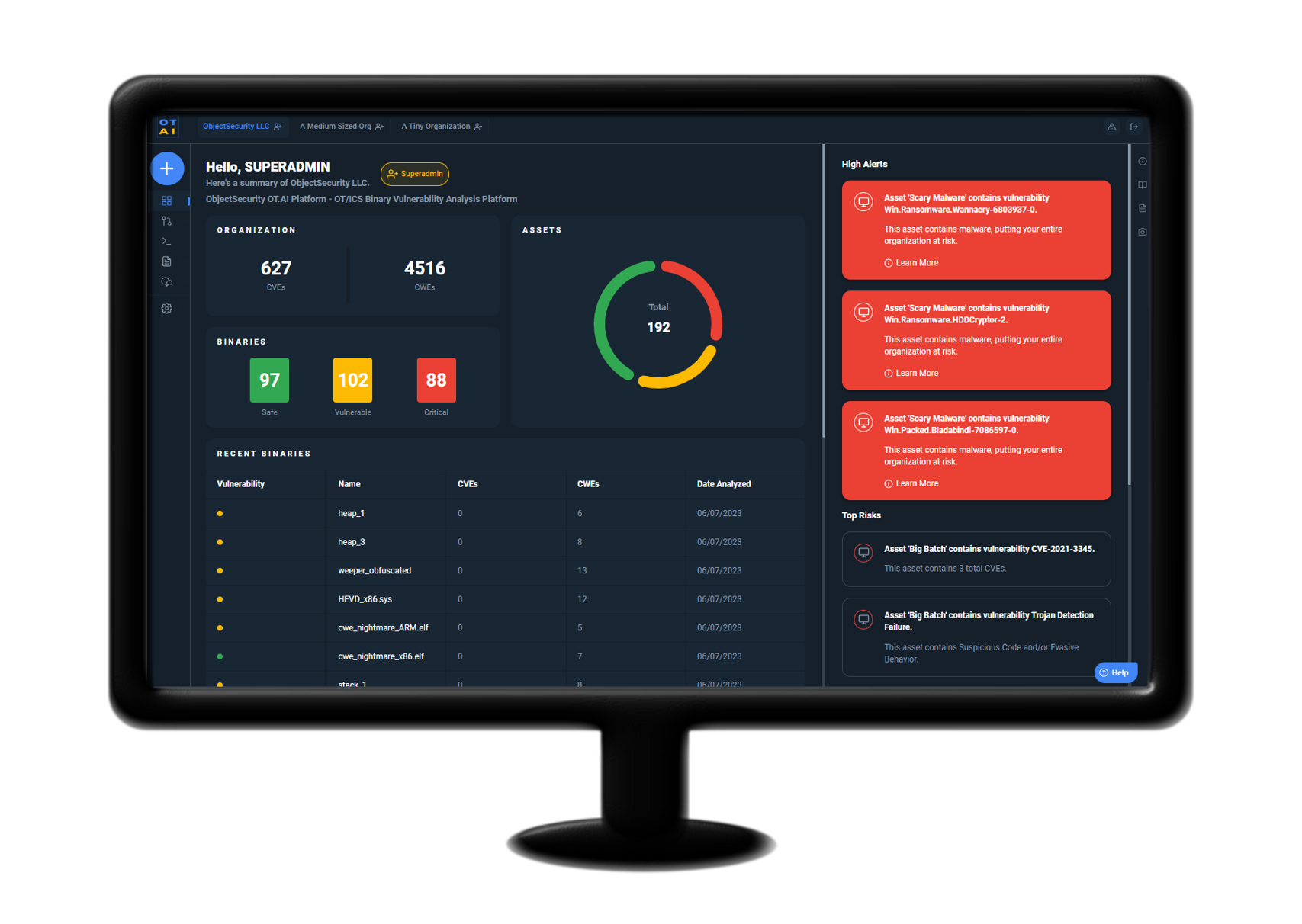
ObjectSecurity OT.AI Platform
Operational Technology (OT) / Industrial Control System (ICS) Asset Binary Vulnerability Analysis and Reporting
Proactively protect your critical industrial infrastructure by preventing OT /ICS cyber attacks and production downtime.
$2
million
per Episode for Unplanned Production Downtime
80%
attacked
OT/ICS Companies Experienced Ransonware Attacks
~40%
vulnerable
OT/ICS Assets Are Too Fragile for Monitoring
Rapidly Find and Report Zero-Day and Published Cybersecurity Vulnerabilities in Industrial Software Code
An estimated 20-70% of OT/ICS assets cannot be monitored for behavioral attack activity. Legacy, fragile, and end-of-life HMIs and PLCs are exposed to cyber attacks.
ObjectSecurity OT.AI Platform addresses the Purdue Model Levels 0, 1, and 2 with automated binary vulnerability analysis for many PLCs, HMIs, Controllers, SCADA Systems, and Historians – including XIoT Industry 4.0 assets.
ObjectSecurity Government Cyber Defense 12 Years of Research & Development
to Protect Your OT/ICS Critical Infrastructure
ObjectSecurity Binary Code Analysis Science
ThreatAI™
Novel Artificial Intelligence and Binary Code Analysis Science Combined for Reliable and Confident Results
Binary Fuzzing
AI + ML Incremental Delta AnalysisSpeed
Increases Confidence and Speed of Vulnerability Analysis
Lineage Analysis
Superset Binary DisassemblyNo False Results
Eliminates False Vulnerability Analysis Results
Attack Vectors
FLIRT and Taint AnalysisReveals Zero-Day
Finds Unpublished Vulnerabilities Based on Exploitability

Weak Pointer
Rapid Weak Pointer IdentificationAuto ID
Automates ID of Known Binary CVEs and CWEs
Deep Analysis
Memoization Across AnalysesOutpaces Attackers
Searches Code Deeper Than the Attack Surface
Whole-System
Layered Annotative ExecutionHolistic View
Provides a Holistic View of Complex OT Asset Vulnerabilities
Proactively Secure
Industrial Critical Infrastructure
Follow Standards: NIST 800-53, NIST 800-82, and ISA/IEC 62443-3-3 and 62443-4-2
Use Cases
Detecting the xz-utils Backdoor with Automation
In this ObjectSecurity blog post, we discuss how automated binary vulnerability analysis helps detect advanced attacks such as the recently discovered "xz-utils backdoor", which [...]
Automating Binary Exploit Detection using the ObjectSecurity OT.AI Platform
Binary analysis is essential for protecting software, running on various devices, when you do not have access to resources such as source code, open [...]
PRESS RELEASE: Army awards ObjectSecurity $1M Vehicle Cybersecurity Contract
San Diego, Calif. – March 20, 2024 – ObjectSecurity, a leader in solving complex, evolving defense and industrial cybersecurity and supply chain risk challenges, today [...]