
OpenPMF 4.0 User Manual
excerpt of Version 1.0 - December 2018 - © ObjectSecurity LLC - all rights reserved - questions? contact us
Introduction
The future is now
Today’s information age would have felt like out of a sci-fi movie to someone 20 years ago. More data has been created in the past two years than in the entire previous history of the human race. 1.7MB of data is created for every human per second. Within 4 years, we will have generated 44 trillion gigabytes of data, and will have 50 billion smart connected devices. Most of the data is managed by enterprise and governments. For example, a third of all data will pass through the cloud. Every angle of daily life of citizens, enterprise, and government is touched by IT.
With that progress comes a great need to control access to data and IT systems. We increasingly rely critically on IT to work as expected and on data to be protected. Our physical safety, our health and well-being, our economy and business success, our national security and defense, and much more depend on it.
Conventional cybersecurity – not good enough anymore
Unfortunately, today’s cyber security is simply not good enough to protect us, and our data and systems, from attack. This is shown by many high-profile hacks in recent times across pretty much all industries.
Because security is not good enough, many organizations cannot fully leverage the benefits of IT automation, and cannot protect well from breaches of their increasingly large and interconnected IT landscapes.
Incremental progress in the cybersecurity industry is not nearly fast enough to protect users and organizations from attack. To really ‘move the needle forward’, we need to change how we do security today.

Conventional cybersecurity - not good enough anymore
Technical policy management – many challenges
Security policy management is hard
When securing your organization, including both users and your interconnected IT systems, are you going to manually configure & maintain all security rules and configurations everywhere?
One of the key problems for enterprise (and governments) today is that it is difficult to figure out and manage security requirements. Once these so-called “enterprise security policies” are figured out, it is even harder to technically implement them so they actually protect today’s complex, interconnected IT landscapes. There is a large gap between how human security professionals think about security policies, and how technical systems implement them. This is especially true for access control policies, which lie at the heart of cybersecurity.
Access Control is hard to manage
In particular, it is hard to manage and implement access control that gives everyone (and every device) the access they need but no more, because this requires many complex, dynamic access rules. Historically, it has been terribly painful or just plain unmanageable. Where does the policy come from? Who can write the matching technical policy rules? Who can maintain them despite dynamic changes? Who can verify policy correctness and compliance?
There are too many overlapping rules and configurations in too many places, and too many changes to do this manually. Also, the security policies you actually want are too complex to maintain manually across many systems, and they often do not even support the implementation of the policies you wanted. For example, user identities, roles and privileges need to be configured and maintained with Identity & Access Management (IAM) systems. Additionally, firewalls rulesets and other network equipment, operating systems security, database security, application security, web security etc. all need to be configured and secured in their own right.
Access control is hard to manage
Too hard to do it manually
Today’s overworked IT departments do not have the resources to author and maintain too many technical access rules, or manually integrate tools into their IT landscape. Security administrators are facing a “lose-lose” situation, especially for access control: Either, today’s security tools help implement access control that is too simplistic to actually reflect the enterprise security policies. For example, today often inadequate access controls are implemented (often purely based on identities and roles). Or they try to manually implement enterprise security policies, which is unmanageable, especially because today’s connected IT landscapes are ever-changing and evolving. It is also not auditable. And human configuration errors happen - the needed policies are too hard to author and maintain and too hard to technically integrate and implement. Multi-$bn are wasted every year world-wide in staff and consultants costs, and costs of security breaches and non-compliance.
Of course enterprises already have a bunch of tools available to manage access, especially identity & access management products. However, these are better at managing things like identities, roles, authentication, account provisioning and deprovisioning etc. Most of them are not so useful for managing access control policy rules. And the access control they can provide is usually not very adaptive, and cannot be enforced consistently across today’s typical hodgepodge IT landscape. On the other end of the spectrum, there are some fine-grained access control vendors, but they are often unmanageably complex, requiring administrators to manage complex and numerous access policies.
What’s needed: Policies for humans, and policy automation.
How humans ‘do policy’
Access control needs to be human-manageable and adaptive, meaning decisions are based on dynamically changing context. Humans think of security policies in few concepts that are non-technical, concise, general, and rich. Machines, on the other hand, are good at processing the opposite: many detailed, specific technical rules and configurations.
At the core of the problem is that humans intuitively “think policy” differently. When you abstract away the underlying technical complexities, the policy that you wanted isn’t usually all that complex and long if you author it in human-intuitive concepts and terms. Humans are usually better at expressing policies in intuitive, “undistorted”, non-technical concepts, in general concepts, and in rich concepts (rather than in detailed technical terms). Policies get much simpler for humans this way.
| How humans ‘do policy’ | How machines ‘do policy’ |
|---|---|
| Non-technical, concise concepts | Technical |
| Few policy rules | Many rules in many places |
| Imprecise | Precise |
| General concepts | Many details |
| Rich concepts | Specific, often simple concepts |
The need for security policy automation
So what’s the solution? Wouldn’t it be logical to use an automated tool to bridge the gap between human-manageable, intuitive policies and the matching detailed technical rules and configurations. This would allow security administrators to author policies in very generic terms. The tool should then automatically fill in the technical details, and enforce the policy.
For example, administrators should be able to author policies such as:
-
“only allow a selection of the detected information flows and block everything else”
-
“all analysts can access all data about any suspect they are tasked to investigate, and about all other suspects that are within 3 hops social proximity of that suspect”
Such a “security policy automation” solution needs to automatically bridge the gap between such human-understandable, intuitive policies and the matching detailed technical rules and configurations. It should automatically generate technically enforceable technical rules and configurations (esp. for access control policies). It should also automatically test policies, produce documentation, and monitor security activity.
How would such a tool achieve security policy automation? By importing existing information sources, and using them to fill in the technical details. For example, it could import information about users, roles, applications, systems, networks, network traffic, and much more.
The remainder of this whitepaper describes how ObjectSecurity OpenPMF™ 4.0 security policy automation helps you achieve such powerful security policy implementation with effortless management.
OpenPMF
OpenPMF™ 4.0 Security Policy Automation stops security breaches with powerful policy enforcement, and makes security policy manageable through automation. OpenPMF is an “umbrella” platform for security policy management. It allows organizations to implement rich policies with consistency – organization-wide “in depth” across many technologies and layers.
OpenPMF automatically bridges the semantic gap between human intuitive generic security policies and technical implementation. Author rich, generic, advanced policies. Automatically calculate the matching technical rules & configurations.
OpenPMF lets you do this in a way that is easy to implement, manage, audit: You can author and maintain powerful yet intuitive security policies across your IT landscape , including for example Attribute Based Access Control (ABAC) based on rich, customizable attributes such as location, time and context. OpenPMF automatically calculates the matching technical enforcement rules and configurations for you - automatically bridging the ‘semantic gap’ between human intuitive generic security policies and the detailed technical implementation.
OpenPMF reduces risk/costs, improves security & compliance, and enables smarter business. With OpenPMF™ 4.0 Security Policy Automation, you can enforce powerful technical security policies that are easy to manage. Maximum security. Minimum effort.
Why you need OpenPMF
This is why OpenPMF should be your overarching security policy management solution:
- OpenPMF Security Policy Management Platform stops security breaches with powerful policy enforcement. OpenPMF™ makes security policy manageable through automation.
- OpenPMF automatically bridges the semantic gap between human-intuitive, generic security policies and technical implementation: Author rich, generic, advanced policies. Automatically generate the matching technical rules & configurations.
- OpenPMF is a security policy automation “umbrella” that lets you
manage “one truth of the policy” in generic, expressive, intuitive
terms - OpenPMF imports existing information that makes policy
automation easier, using its customizable importers - OpenPMF generates and enforces the matching low-level policies across your IT landscape via its own enforcement infrastructure and via customizable exporters into third party products
- OpenPMF monitors security, and generates compliance documentation automatically.
- OpenPMF also lets you test policies before deployment.
- OpenPMF is robust and scalable regardless
of the complexity of your IT landscape today and what it evolves to
tomorrow.
Unique features
-
ObjectSecurity OpenPMF lets you easily author generic and advanced security policies. It enables you to maintain “one truth” of the undistorted, feature-rich, expressive policies. OpenPMF automatically calculates the matching technical rules & configurations for the underlying IT landscape, integrating either via OpenPMF’s own enforcement software agents, or via rapidly customizable exporters to configure third party products.
-
OpenPMF is powerful and scalable: such generic policies will not need to be changed often, even if your IT landscape changes! OpenPMF simply re-calculates the technical updates for you!
-
Unlike competing technologies, OpenPMF makes advanced access policies both manageable and implementable. It integrates out of the box with numerous standards and technologies, and automates much of policy authoring and enforcement.
Unique benefits
-
OpenPMF helps you implement and manage better access policies: you can robustly implement the necessary access control policies across your IT landscape based on rich, customizable attributes including location, time and context.
-
OpenPMF makes access control mode effective, auditable and manageable across your interconnected IT landscape for all stakeholders. It reduces cost, and improves security and compliance. It also speeds up and simplifies security implementation, maintenance, and testing. It is often implemented as part of Identity & Access Management (IAM) initiatives, which all major enterprises and governments have.
OpenPMF has been deployed for over a decade across several industry verticals. ObjectSecurity as a vendor is here to stay: The company has been in the market for 18 years. Our flexible “OpenPMF” product is available as an on-premises product and a flexible SaaS service. It can be customized, to import whatever information sources you have, and to export access control policy configurations into whatever applications and systems you have.
OpenPMF™ Makes Security Policy Manageable Through Automation.
ObjectSecurity’s OpenPMF security policy management platform stops security breaches with powerful policy enforcement. It gives you powerful security policy implementation that is also effortless to manage.
It allows you to improve protection, monitoring, testing, and documenting – for your information, users and devices. OpenPMF™ turns human-manageable security policies automatically into the matching preventive technical implementation.
OpenPMF lets you manage security policies in customizable terms that matter to your organization. OpenPMF ensures policies are manageable even if IT landscapes are large and change dynamically. The result is a significant cost saving, especially with respect to maintenance.
OpenPMF Policy automation roundtrip
Concept
One of the central concepts behind OpenPMF is its patented “policy automation roundtrip”, which - in its basic form - goes through the following three steps:
- Import information about your organization’s users, systems, applications, networks, network traffic, application traffic, etc. In OpenPMF this is called “functional system description” (note that this includes user information, for example from identity management systems).
- Author intuitive security policies using generic policy building blocks and terms, including terms that are mapped to higher level, more human-intuitive concepts, as well as wildcards and other features. One key objective of OpenPMF is to allow human policy authors to state policies in the most intuitive, most generalized way possible.
- Generate technical enforcement based on the authored intuitive security policies and the imported information. OpenPMF uses a unique, patented technique called “model-driven security” to “fill in the details” in the authored policy with matching pieces of information gathered from the imported information.
The following diagram illustrates the three steps:
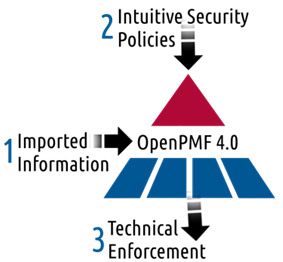
OpenPMF policy automation round trip concept
Wikipedia explains the underlying scientific concept “model-driven security” as follows:
The general concept of Model-driven security in its earliest forms has been around since the late 1990s (mostly in university research), and was first commercialized around 2002. There is also a body of later scientific research in this area, which continues to this day.
A more specific definition of Model-driven security specifically applies model-driven approaches to automatically generate technical security implementations from security requirements models. I particular, “Model driven security (MDS) is the tool supported process of modelling security requirements at a high level of abstraction, and using other information sources available about the system (produced by other stakeholders). These inputs, which are expressed in Domain Specific Languages (DSL), are then transformed into enforceable security rules with as little human intervention as possible. MDS explicitly also includes the run-time security management (e.g. entitlements/authorizations), i.e. run-time enforcement of the policy on the protected IT systems, dynamic policy updates and the monitoring of policy violations.”
Model-driven security is also well-suited for automated auditing, reporting, documenting, and analysis (e.g. for compliance and accreditation), because the relationships between models and technical security implementations are traceably defined through the model-transformations.
Policy automation in OpenPMF
In practice, the OpenPMF policy automation roundtrip usually goes through more detailed steps, as shown in the following 8-step diagram:
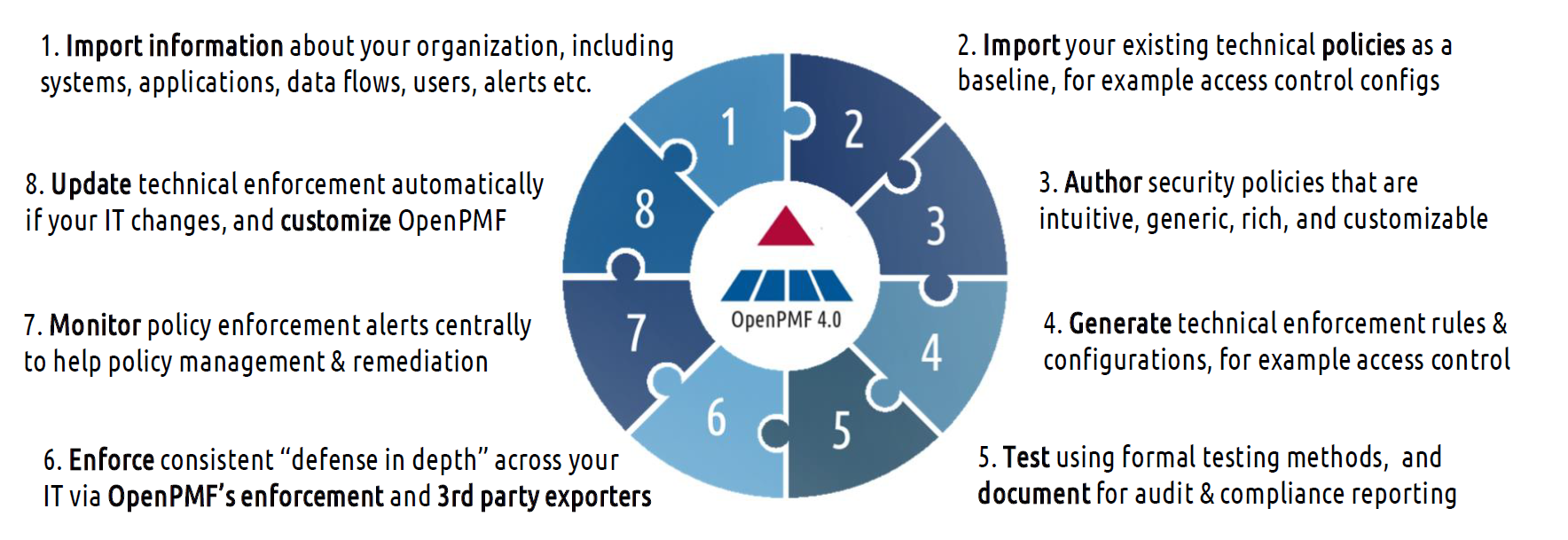
OpenPMF policy automation round trip
Import information about your organization, including systems/applications, networks, data flows, users, alerts etc.
OpenPMF has a rapidly customizable, standards-based importer interface that lets you import various information sources, which simplifies policy authoring: OpenPMF then lets you author policies in generic terms, referring to selections of imported data. For example, you can allow only certain information flows between certain applications, or between certain systems. Such rule elements can be combined with other rule elements, including user identities, roles, proximity, and more.
The crucial benefits are that the authored policies are simple and generic, and do not have to be changed if the imported information changes. OpenPMF simply detects the changes when re-importing and updates the policies accordingly.
OpenPMF supports many importers out of the box. For example, you can import information about your networks and applications using OpenPMF’s network traffic log importer. Or you can import information from your identity management system via LDIF. Or import security alerts from Syslog. The imported information can be analyzed, selected, and visualized conveniently in a user-friendly UI.
OpenPMF’s ingestion of those other information sources is also easily customizable so you can import your particular organization’s information.
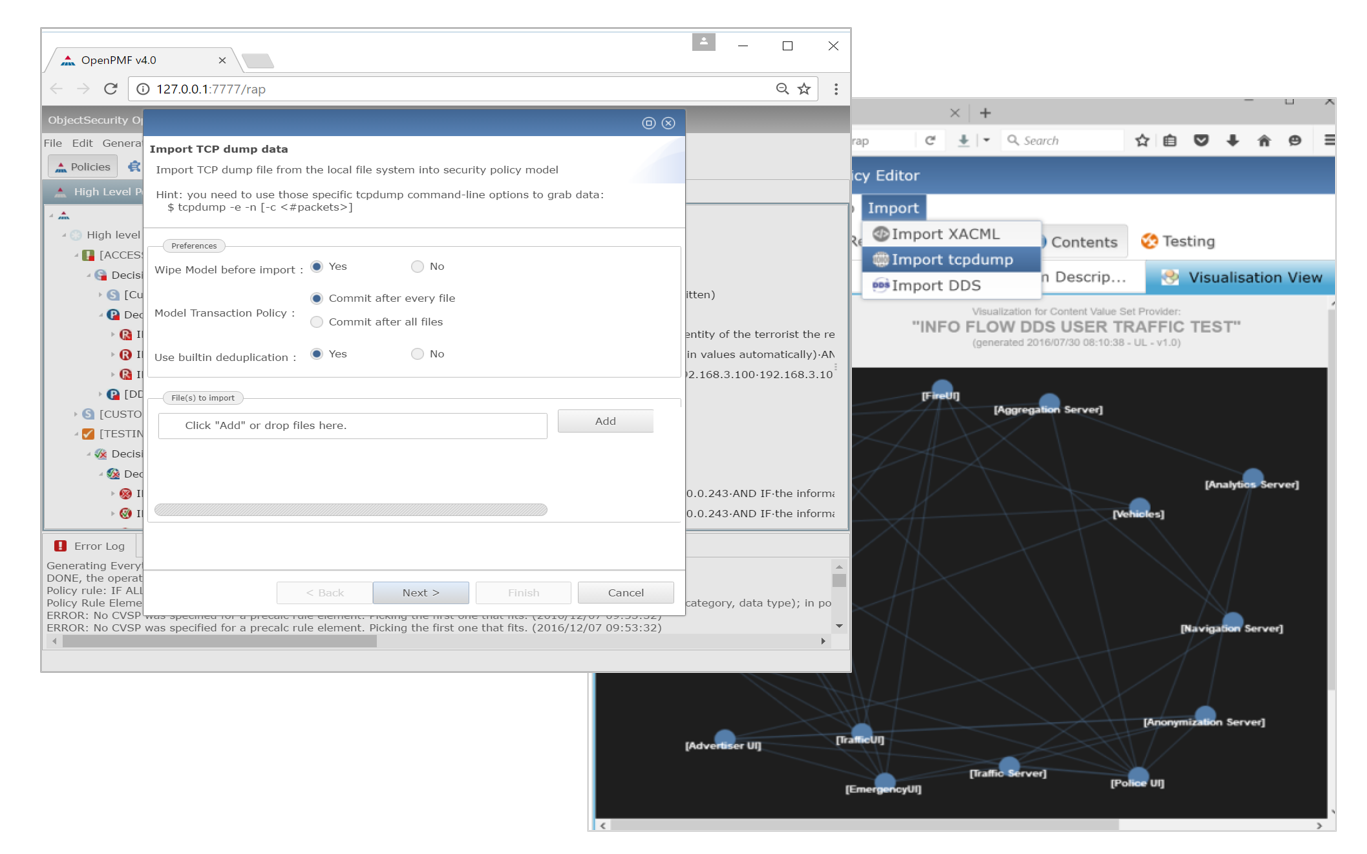
1. Import information
Import your existing technical policies as a baseline,for example access control configurations
As already described, OpenPMF has a rapidly customizable, standards-based importer interface that lets you import various information sources making life easier during policy authoring.
In order to ensure you do not have to start from scratch, OpenPMF allows you to import existing security policies that are in place throughout your IT landscape.
For example, you can import:
- access policies specified in OASIS XACML
- policy information from identity management systems (via LDAP LDIF)
- network security policies defined in host firewalls and domain boundary controllers (iptables etc.)
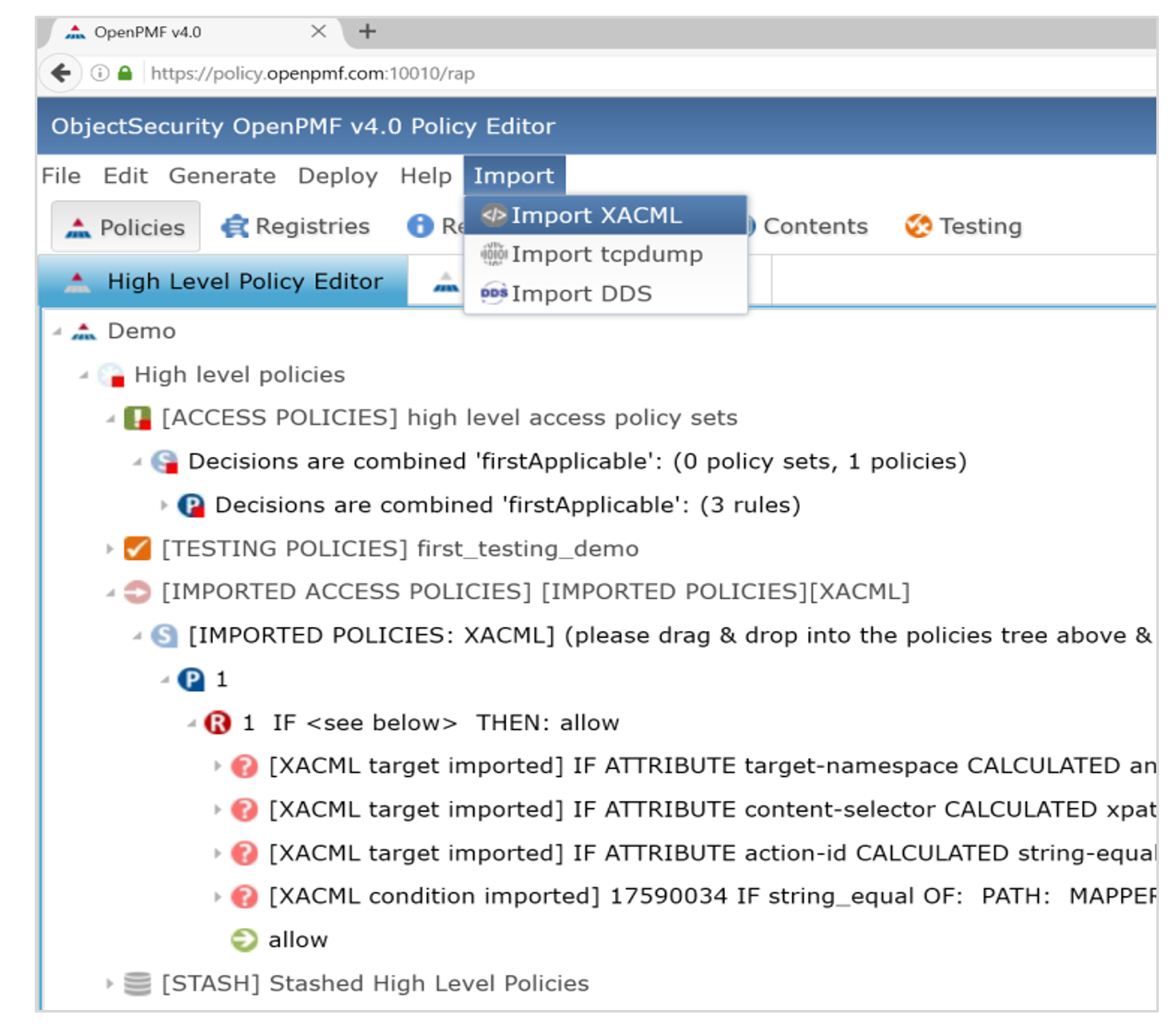
2. Import policies
Author security policies that are intuitive, generic, rich, customizable
OpenPMF lets you author policies in generic, intuitive, rich concepts, using terms you choose. Security professionals can easily edit “high-level” access control (and other) policies in OpenPMF’s easy-to-use, flexible policy editors (graphical editor, and smart text editor). Users only have to author a few intuitive, generic “high-level” policies compared to the multitude of technically enforced “low-level” policies, making OpenPMF a solution that saves money and time.
OpenPMF even allows you to write policies using attributes and rule elements that are not readily technically enforceable, and automatically calculates mappings to technically enforceable, available attribute sources, calculation sources, and mapper sources.
For example, if users want to author policies that grant or deny access based on whether the requestor’s current location is in the US or EU (e.g. for privacy enforcement), but only the geolocation can be obtained from the request context, mappers can be integrated into OpenPMF that map between US/EU, country code, and geolocation.
As another example, you can automatically “whitelist” application interactions that have certain characteristics and block anything else. This unique feature empowers users to author policies in more generic, intuitive terms without going near the complex, numerous low-level technical policies.
The ‘vocabulary’ used to author policies, such as attributes and calculations, is fully customizable, and the corresponding data can be flexibly imported from your organization’s existing data sources (e.g. HR systems, logistics systems, task management systems).
The web-based editor and the underlying data models are standards based. The editor itself auto-configures after even a major customization of OpenPMF, resulting in a rapid and straightforward implementation.
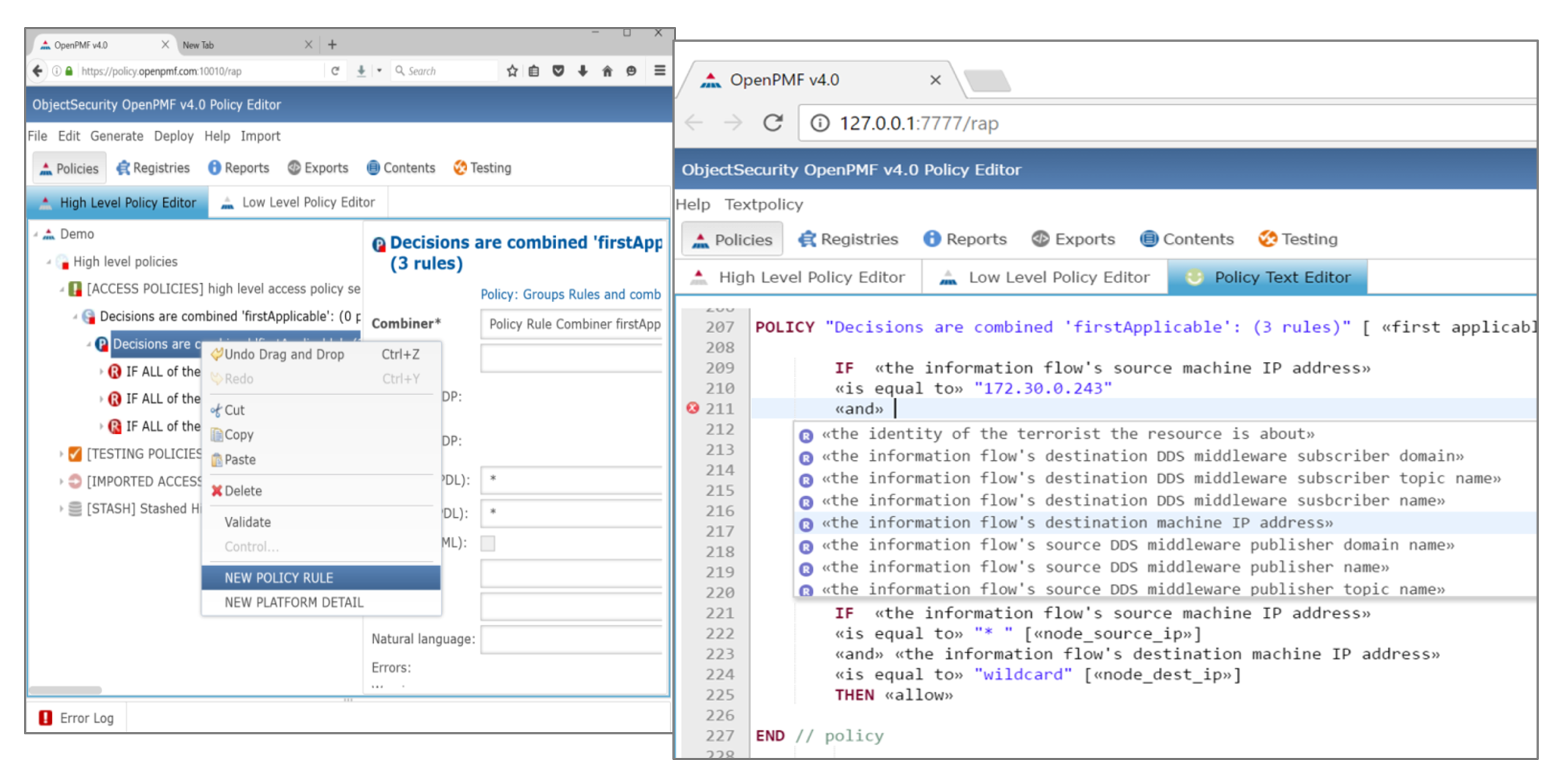
3. Author policies
Generate technical enforcement rules & configurations,for example access control
OpenPMF automatically generates “low-level” technical policy implementation from the authored generic, intuitive expressive “high-level” policies and other - ideally already existing - information sources.
During the generation process, OpenPMF uniquely bridges a “semantic gap” between the human-intuitive high-level policies and the matching low-level technical policies.
The benefits are that the high-level policies:
- remain undistorted from the technical details ofthe underlying IT landscape;
- can be reused. For example, it is possible to define generic templates for enforcing specific aspects of the GDPR or othe regulations
- do not have to be updated if the technical detailsof the underlying
IT landscape change (such as.re-configuration of interactions, user role
updates
etc.)
4. Generate technical policies
Test using formal model checker methods, and document for audit & compliance
Test using formal model checker methods
OpenPMF includes an advanced policy testing feature based on formal methods (symbolic model checker, combinatorial testing). Users can simply author policy properties they would like to test for (in the context of imported information about systems, information flows, users etc.). Users can then simply run a test that proves/disproves whether policies will have the intended effect.
This feature uses a formal combinatorial model checker. It is based on years of scientific development by the National Institute of Standards and Technology (NIST). ObjectSecurity won Phase 1 and phase 2 of a NIST SBIR to develop, extend, and commercialize this feature (see objectsecurity.com/nist).
Document for audit & compliance
Regardless of their technical acumen, OpenPMF’s documentation feature provides users with a straightforward and easily understood documents about the policy and its implementation.
-
Natural language documentation: OpenPMF automatically generates a natural language document about your policy at the click of a button. This version of the policy is easy to read and understand, making it easier to understand the policy.
-
Compliance documentation: OpenPMF automatically documents every step its algorithms have taken in an a natural language report, which can be used by audit and compliance to understand how the technical policy was generated from the authored high-level policies. This especially supports audits by 3rd parties and non IT experts, for example laywers.
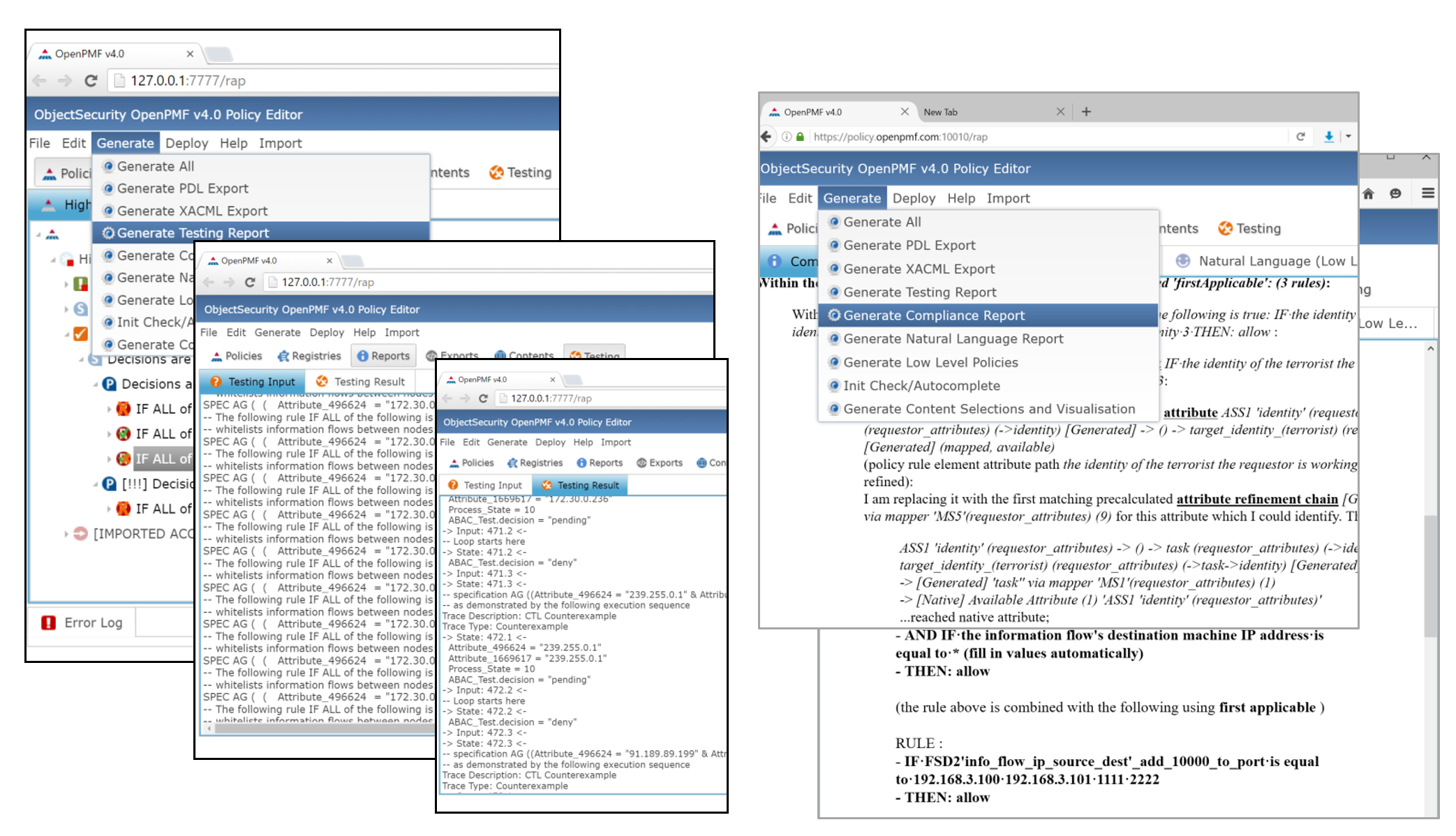
5. Test and document
Enforce consistent “defense in depth” across your IT landscape – via OpenPMF’s enforcement – and via 3rd party exporters
1) OpenPMF’s own enforcement infrastructure supports many technologies out-of-the-box, and other technologies on demand
OpenPMF comes with its own enforcement infrastructure, which includes a Policy Access Point (PAP) and local software agents (Policy Decision Points, PDPs and Policy Enforcement Points, PEPs) that can be installed on the to-be-protected systems or on network equipment. OpenPMF distributes technical rules to these software agents at the click of a button.
Each local software agent then intercepts information flows (e.g. all messages going in and out of its host system and applications), fetches the necessary information to make a decision, and enforces that decision. Decisions can be for access control (“allow”/”deny”) decisions, monitoring (“log”), or customized actions.
OpenPMF supports manageable and effective Attribute-Based-Access Control (ABAC) security enforcement with push-button updating to protect systems that do not themselves provide adequate security features.
OpenPMF supports many technologies out-of-the-box, and other technologies on demand, including for example: host-based firewalls, OSGi middleware, web app servers, DDS, CORBA/CCM, SOA BPMS etc. (objectsecurity.com/supported-technologies).
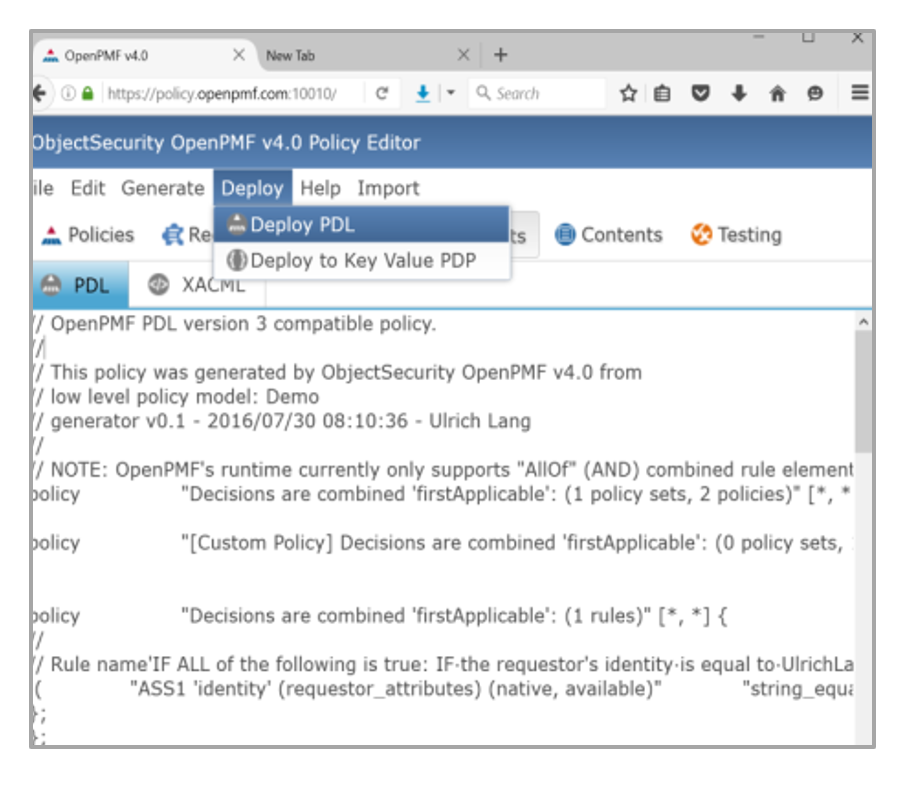
6a. Enforce using OpenPMF's enforcement runtime
2) Export & configure third party products and features using OpenPMF’s rapidly customizable exporter
OpenPMF also has a flexible, rapidly customizable, standards-based export design that can be configured to export low-level policies into 3rd party security products and features.
Thanks to this customizable exporter feature, OpenPMF can configure security of most systems and applications without the need to install software locally, thus saving time and money.
OpenPMF essentially becomes an overarching “security configuration management system” for the organization, which can be used alongside overarching Identity & Access Management (IAM) deployments.
OpenPMF supports exporting configurations into many technologies out-of-the-box, and other technologies on demand, including for example:
-Host firewalls and network firewalls
-IDS/IPS (syslog)
-OASIS XACML
-Middleware security (e.g. OMG DDS Security)
-…
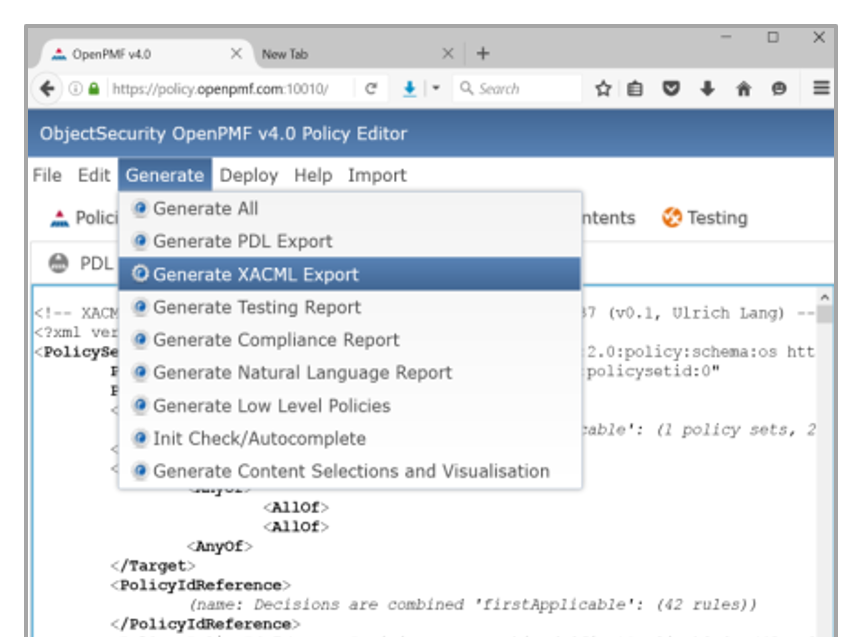
6b. Export to 3rd party products
Monitor policy enforcement alerts centrally to help policy management & remediation
1) Monitor security via OpenPMF’s own runtime.
OpenPMF allows the convenient monitoring of all running enforcement
points in a monitoring dashboard. The dashboard shows the status of the
enforcement point, as well as any alerts produced by the enforcement
point. Alerts are caused by policy violations and by user-configurable
logging policies.
2) Import security alerts
Furthermore, OpenPMF supports importing alerts from 3rd party tools
using OpenPMF’s rapidly customizable importers, for example Snort Syslog
alerts.
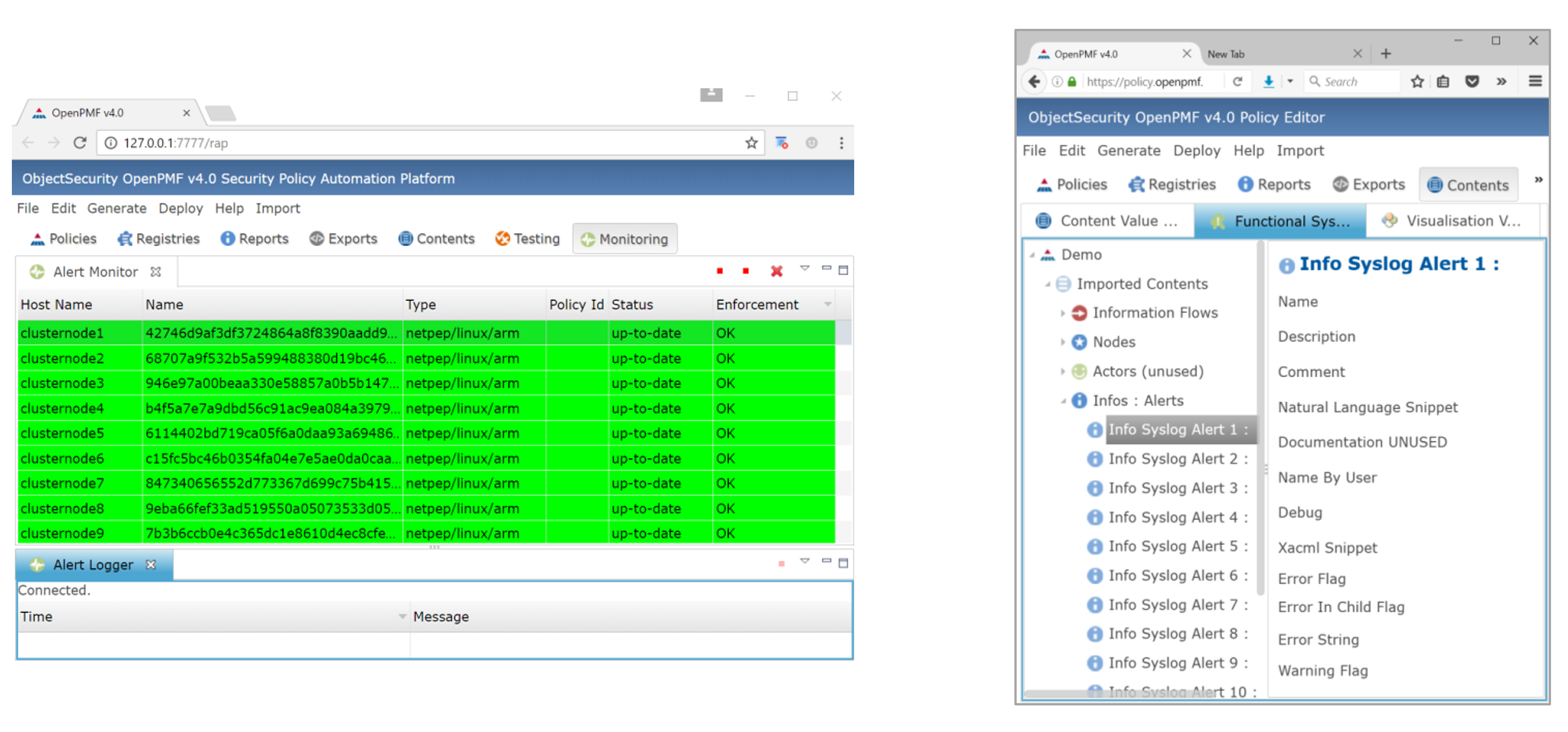
7. Export to 3rd party products
Update technical enforcement automatically if your IT changes and customize OpenPMF
1) Automatically update policies when your IT landscape changes
To update, just re-import information about the changed IT landscape,
and simply regenerate the technical policy at the click of a button.
This capability to auto-update is a major simplification and significant
improvement compared to manually implemented technical security
policies.
It was originally developed to make security policy management easier
for agile Service Oriented Architectures (SOAs), but is widely
applicable today, as IT landscapes become increasingly dynamic and
interconnected (e.g. IoT, microservices, …).
2) Rapidly customize policies and enforcement for your organization
OpenPMF is designed from the ground up to be flexible and rapidly
customizable. Customization and flexibility are absolutely critical
features because every organization has its own set of policies, use
cases, and technologies. There is no “one-size-fits-all” when it comes
to implementing an overarching policy management “umbrella” such as
OpenPMF. Any “one-size-fits-all” products would just end up becoming
point solutions themselves, lacking the critical edges of robustness and
scalability.
You can customize most features of OpenPMF, including policy features, importers, exporters, enforcement.
Furthermore, OpenPMF is based on industry standards (XMI, XML, REST,
Eclipse EMF, MOF, OMG QVT, Xtext, Xpand etc.), making the customization
of the data models, importers, and exporters quite straightforward. For
example, exporters can be developed quickly based on the specific
security products available in your organization.

8. Update easily to reflect changes
. . .
About ObjectSecurity
ObjectSecurity’s mission is to simplify security for the complex, interconnected IT landscapes most organizations deal with today. The company’s primary focus is simplified, automated security management and secure IT application integration, led by its core product – OpenPMF 4.0, the leading security policy automation platform. OpenPMF 4.0 stops security breaches with powerful policy enforcement through patented “model-driven security” automation.
Launched in 2000 by CEO/Founder Ulrich Lang, the company has two independently operated entities: ObjectSecurity LLC in San Diego, CA, and its European company, ObjectSecurity OSA GmbH, near Berlin, Germany. The employee-owned company works with partners and clients in more than 25 countries across the globe.
For more Information
- ObjectSecurity OpenPMF Security Policy Auditor™: objectsecurity.com/auditor
- ObjectSecurity OpenPMF™ 4.0 Security Policy Automation: objectsecurity.com
Copyright
Copyright 2000-2018 ObjectSecurity | All Rights Reserved | Privacy Policy | Terms of Use